- Understanding SSH and Its Importance
- The Threat Posed by Quantum Computing
- What is Post-Quantum Cryptography?
- Transitioning to Post-Quantum Cryptography in SSH
- 1. Algorithm Selection
- 2. Software Updates
- 3. Testing and Validation
- 4. Training and Awareness
- Conclusion
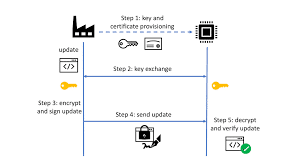
In the rapidly evolving landscape of cybersecurity, the impending arrival of quantum computing threatens to undermine conventional cryptographic methods. As organizations recognize this shift, implementing post-quantum cryptography in Secure Shell (SSH) connections is becoming increasingly critical. Such a transition is essential not only for safeguarding sensitive data but also for ensuring the longevity and reliability of secure communication.
Understanding SSH and Its Importance
Secure Shell (SSH) is a protocol widely used for secure data transmission over unsecured networks. It enables secure remote access and management of systems, making it a cornerstone of modern IT infrastructure. The robustness of SSH largely stems from traditional cryptographic algorithms like RSA and DSA, which are currently susceptible to quantum attacks. The strategic shift to post-quantum cryptography is thus vital to maintain the integrity of SSH connections against future quantum threats.
The Threat Posed by Quantum Computing
Quantum computers leverage the principles of quantum mechanics to perform calculations at unprecedented speeds. Algorithms like Shor’s threaten to compromise widely-used public-key systems by efficiently factoring large numbers, rendering them vulnerable. When quantum machines become mainstream, the cryptographic keys that secure SSH connections using traditional methods will be at serious risk. The need for post-quantum cryptographic algorithms—designed to withstand quantum attacks—has never been more pressing.
What is Post-Quantum Cryptography?
Post-quantum cryptography refers to cryptographic algorithms that are expected to be secure against the capabilities of quantum computers. These include lattice-based, hash-based, multivariate-quadratic-equations, and code-based cryptographic systems. By employing mathematical structures that quantum algorithms struggle to solve, post-quantum algorithms aim to provide a robust alternative for securing communication, including SSH.
Transitioning to Post-Quantum Cryptography in SSH
Implementing post-quantum algorithms in SSH involves several strategic steps. Organizations must first assess their current SSH infrastructure, evaluating the algorithms and key types currently in use. Once the existing framework is understood, transitioning to post-quantum algorithms requires selecting appropriate replacements.
1. Algorithm Selection
Identifying the right post-quantum cryptographic algorithms is crucial. The National Institute of Standards and Technology (NIST) is in the process of standardizing post-quantum algorithms, providing a vetted selection of candidates. Organizations should stay informed about NIST’s recommendations and opt for algorithms that have demonstrated security and performance efficacy.
2. Software Updates
After selecting post-quantum algorithms, organizations must update their SSH client and server software. Many modern SSH implementations are already beginning to incorporate post-quantum features. It is essential to regularly check for the latest software versions, ensuring compliance with cryptographic best practices.
3. Testing and Validation
The transition from traditional methods to post-quantum cryptography is not without risk. Organizations should conduct thorough testing to validate the new configurations. Simulating attacks and assessing the performance of the new algorithms in a controlled environment helps ensure that the updated SSH connections meet security and operational requirements.
4. Training and Awareness
To make a successful shift towards post-quantum cryptography, staff training is equally important. Ensuring that system administrators and users understand the implications and benefits of post-quantum algorithms fosters a culture of cybersecurity awareness. It equips teams with the knowledge needed to effectively manage and secure SSH connections.
Conclusion
The need for implementing post-quantum cryptography in SSH connections reflects a proactive approach to future-proofing cybersecurity strategies. By remaining ahead of the curve, organizations can safeguard their data against the impending quantum threat. The transition involves a careful assessment of current systems, diligent selection of new algorithms, and commitment to ongoing education and adaptation. As quantum technology continues to advance, embracing post-quantum cryptography will ultimately ensure a more secure digital future for all.